Azeeda 2 x 70mm 'Bicicleta de Pedales' Adornos navideños Planos de Madera MDF (CB00088280) : Amazon.es: Hogar y cocina

EcoInventos on X: "Haz tu propia bicicleta de madera contrachapada usando planos e instrucciones gratuitas online. https://t.co/VYniTDBiVV https://t.co/COVZ4AkizS" / X

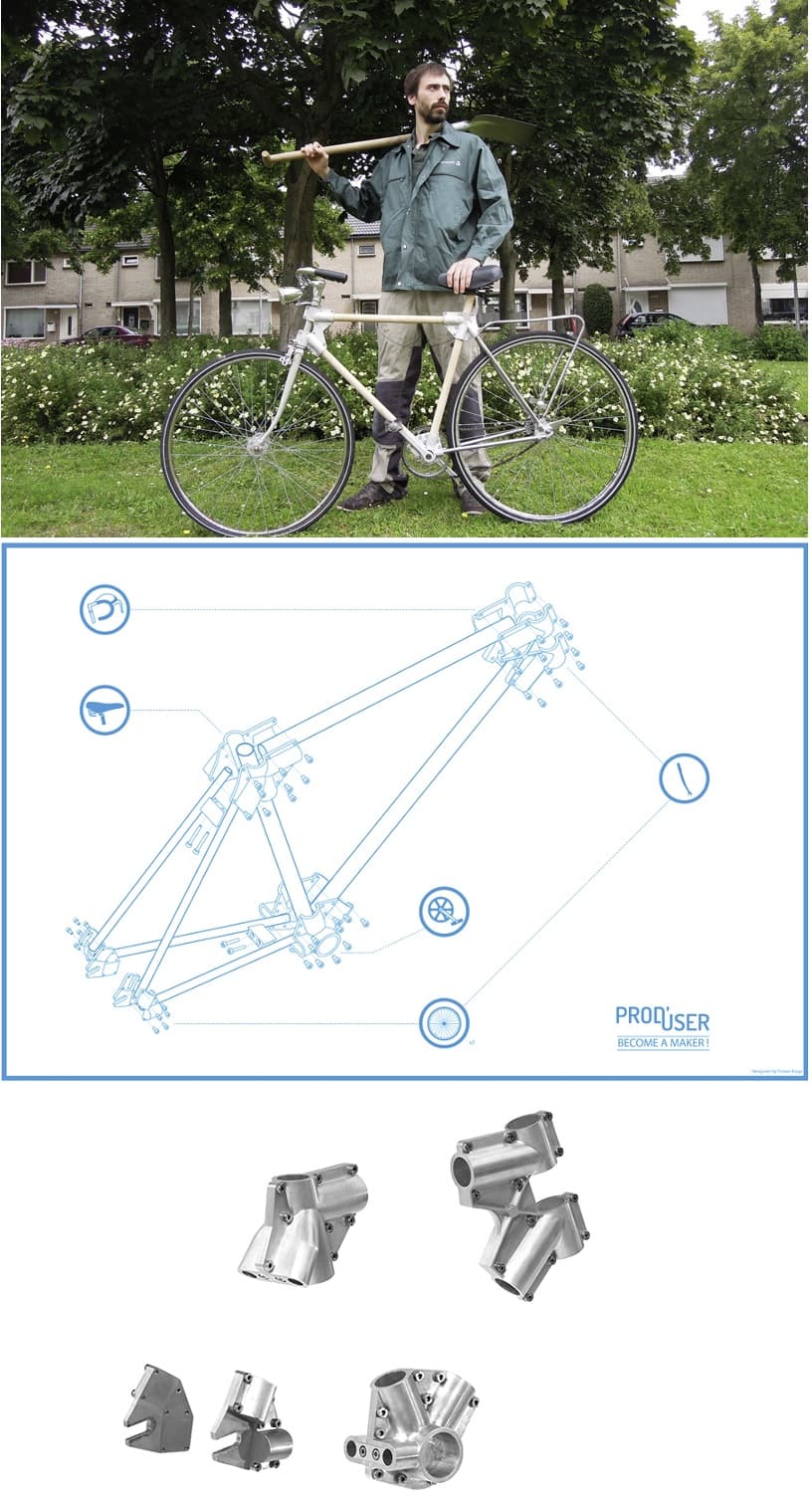
Construyendo una bicicleta sin pedales en madera en el centro de mecanizado - Diseño programación y cursos CNC
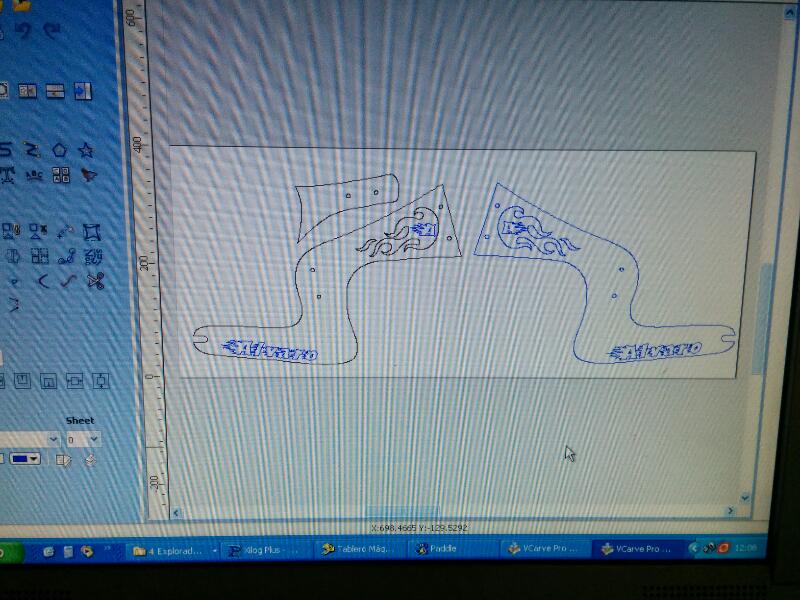
Construyendo una bicicleta sin pedales en madera en el centro de mecanizado - Diseño programación y cursos CNC