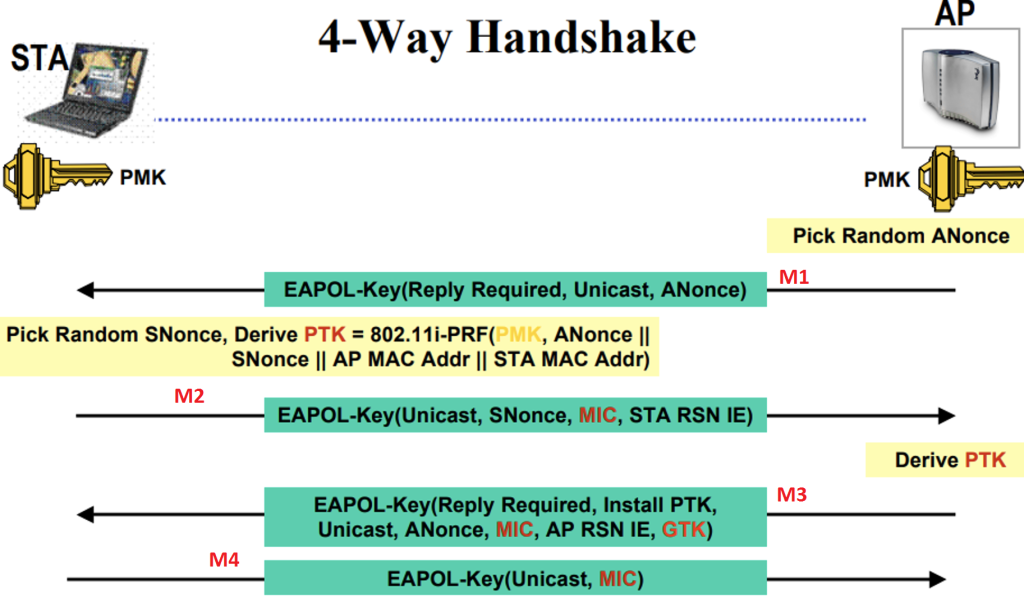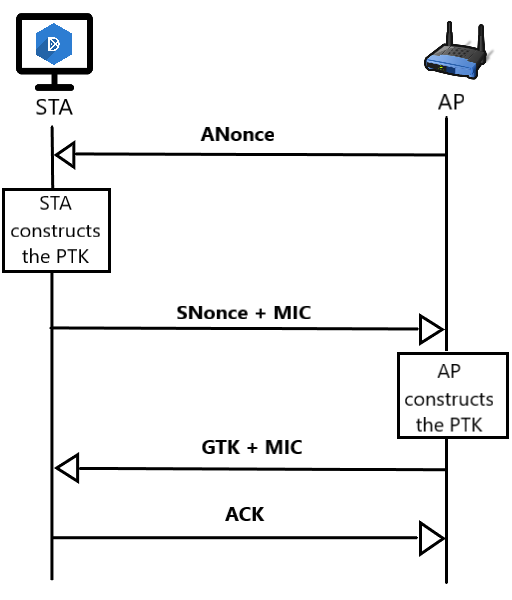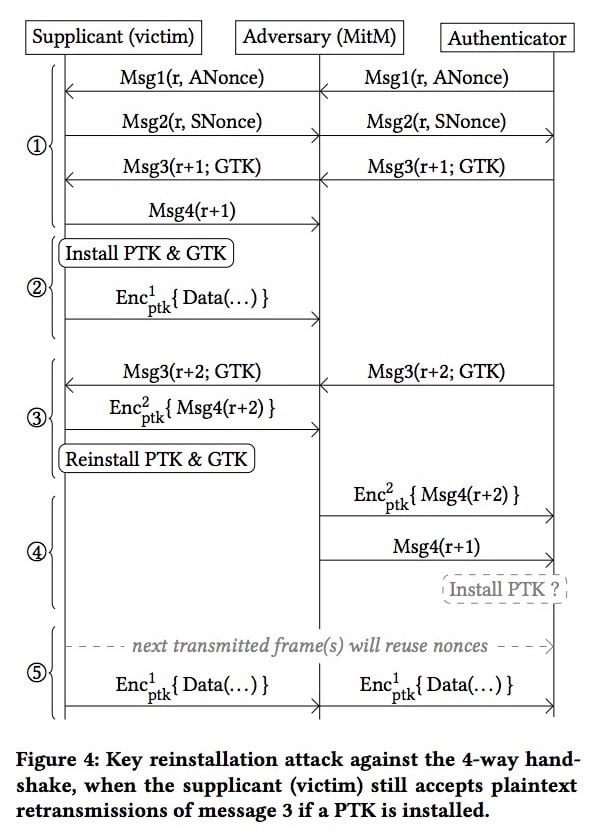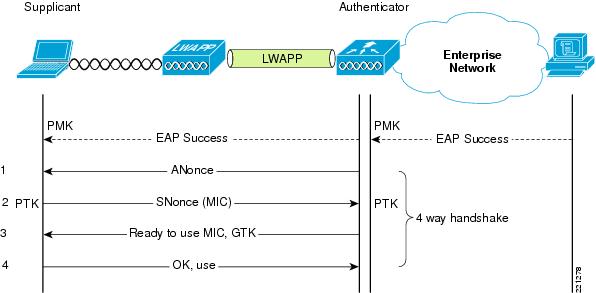
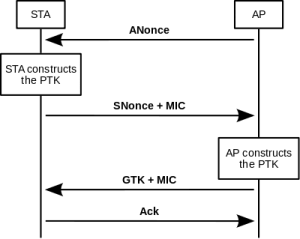
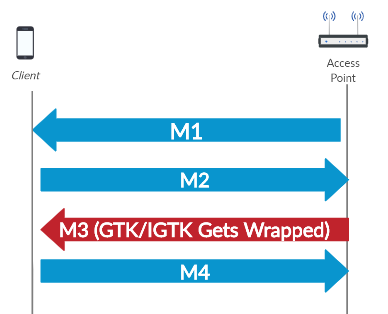
my80211.com - 802.1X LABS - GEORGE STEFANICK - CWSP JOURNEY, (CHAPTER 5 – 4- WAY HANDSHAKE POST#5)- 10/03/2010

Encryption using DES of ANonce in 4-Way Handshake Protocol for Authentication in Wpa2 | Semantic Scholar

Analysis of the i 4-Way Handshake Changhua He, John C Mitchell Stanford University WiSE, Oct. 1, ppt download
Secure Authentication and Four-Way Handshake Scheme for Protected Individual Communication in Public Wi-Fi Networks
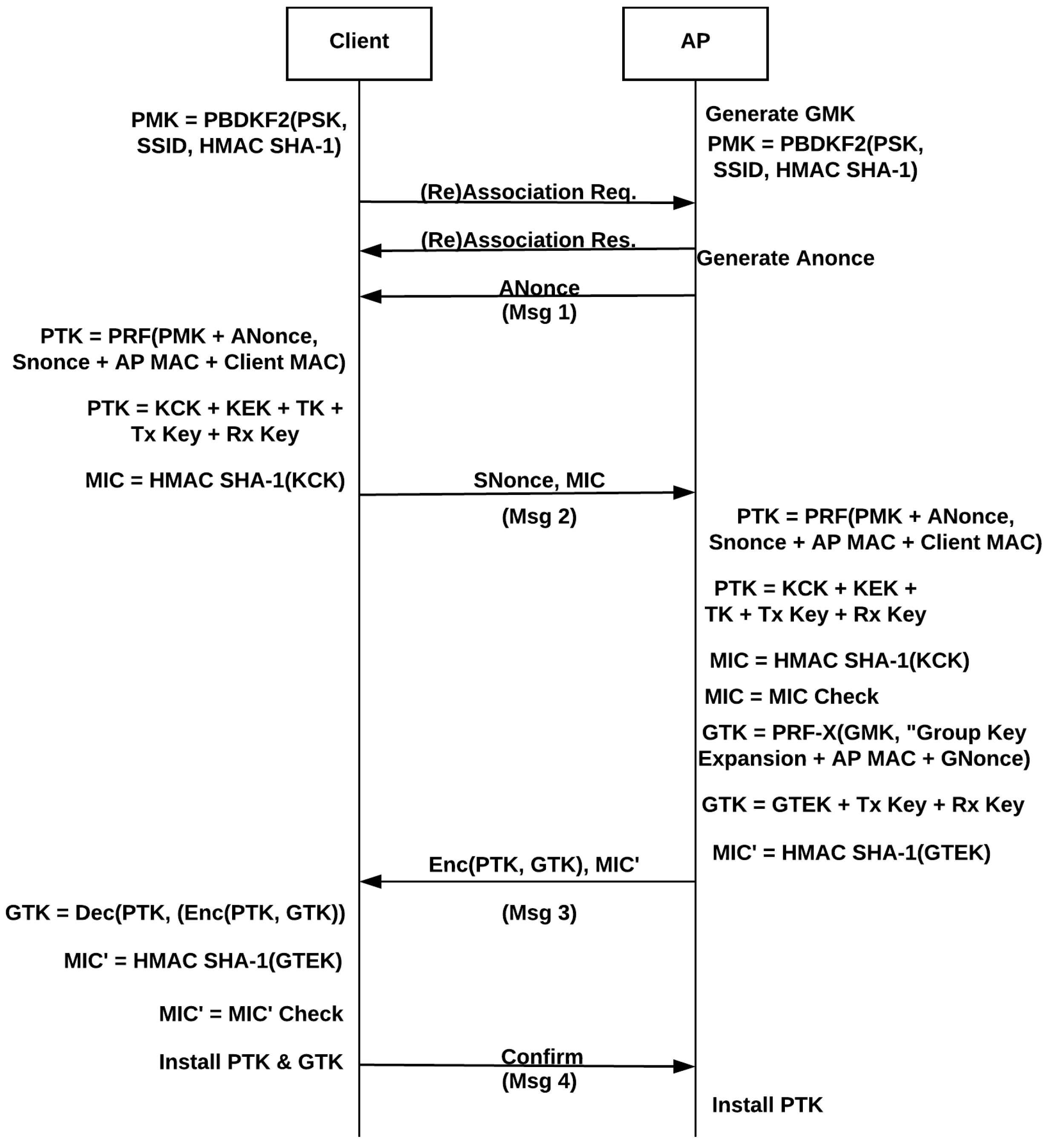


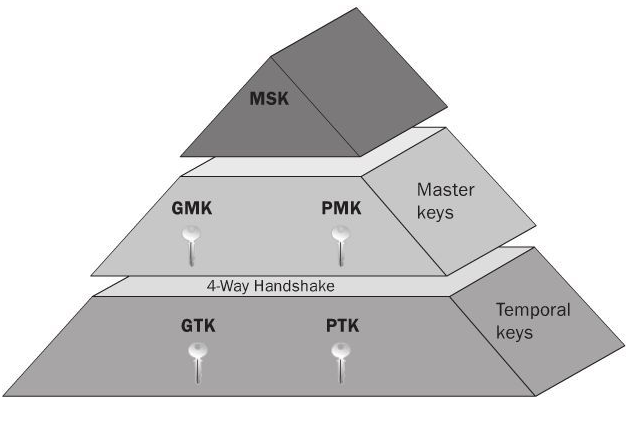



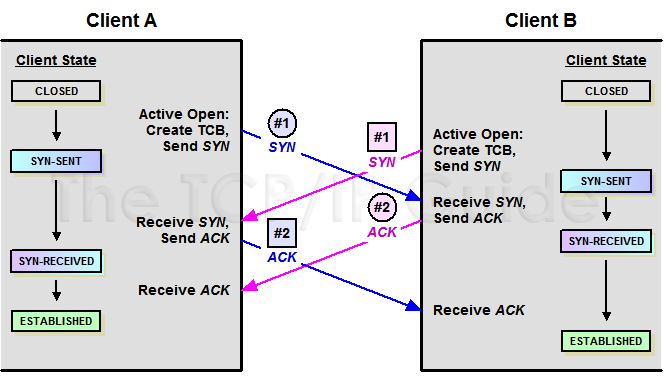
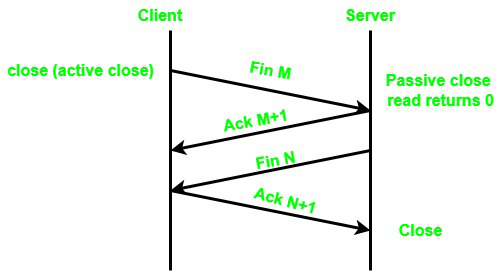
![Network] TCP 3-way, 4-way Handshake Network] TCP 3-way, 4-way Handshake](https://images.velog.io/images/nnnyeong/post/fd5029e1-b84c-4fa3-9f7b-d5f702f1b1b9/image.png)